CYBER THREAT INTELLIGENCE
Always stay a step ahead of the hackers, with cyber threat intelligence. Bolster your defences and be better prepared to prevent or effectively respond to cyberattacks.
- Home »
- Threat monitoring detection response »
- Cyber threat intelligence
What is Cyber Threat Intelligence and how is it used?
Cyber threat intelligence is the range of data and information available within your organisation about past, current and potential cyberattacks on your business. The process involves building a detailed and documented understanding of cyber threats and the motives, tactics, and procedures used by malicious actors. This knowledge is what helps you create robust security defenses, and appropriate incident response.
Get an in-depth view of the range of cyber threats out there.
We put together a compilation of:
- The major cyberattacks in Australia last year, across a number of industries including, healthcare, financial services, technology, and e-commerce
- How they impacted the businesses
- How they could have been prevented
Given several major data breaches in recent times, Australian businesses are highly vulnerable to cyber threats. And an insight into where the next attack might come from is crucial to improve information security practices. With StickmanCyber, you get actionable threat intelligence — it’s timely, provides context, and is understood by the people in charge of making decisions, making it an important part of your organisation’s cybersecurity strategy.
Why Invest in Cyber Security Threat Intelligence?
There are three key types of threat intelligence:
Tactical threat Intelligence
Aimed at identifying simple indicators of compromise (IOCs) like malicious IP addresses, URLs or domain names. It is machine-readable and typically automated through various security software and tools. However, it’s important to note that tactical intelligence is actionable for a few hours or days at best because cyber criminals are continuously changing their tools and methods.
Operational Intelligence
Refers to the collection of knowledge about cyberattacks, events, or campaigns. It helps incident response teams understand the nature, intent, and timing of specific attacks. Unlike tactical intelligence, machines alone cannot collect operational intelligence and human personnel are required to analyse raw data and convert it into a format that is easy to understand and use.
Strategic Intelligence
Documents how events on a global scale - foreign policies, and other long-term movements - can potentially impact the cybersecurity of an organisation. Strategic intelligence provides clarity to an organisation’s threat landscape and is intended to inform high-level decisions made by executives and other decision-makers at an organisation. It is generally less technical and presented through reports or briefings.
| Function | Benefit |
| Security/IT Analyst | Improve prevention and detection technology in the effort to strengthen defences |
| Security Operations Center | Evaluate which incidents need to be prioritised based on risk and impact on the organisation |
| Incident Response Team | Accelerate incident investigations, management, and prioritisation |
| Executive Management | Provides context to the risks the organisation faces and what the options are to address their impact |
Turning visitors into leads.
Take Action Now!
Leverage every past and potential cyber threat to further bolster your defences. Speak to our experts and identify the right cybersecurity solution for your business.
How We Do It
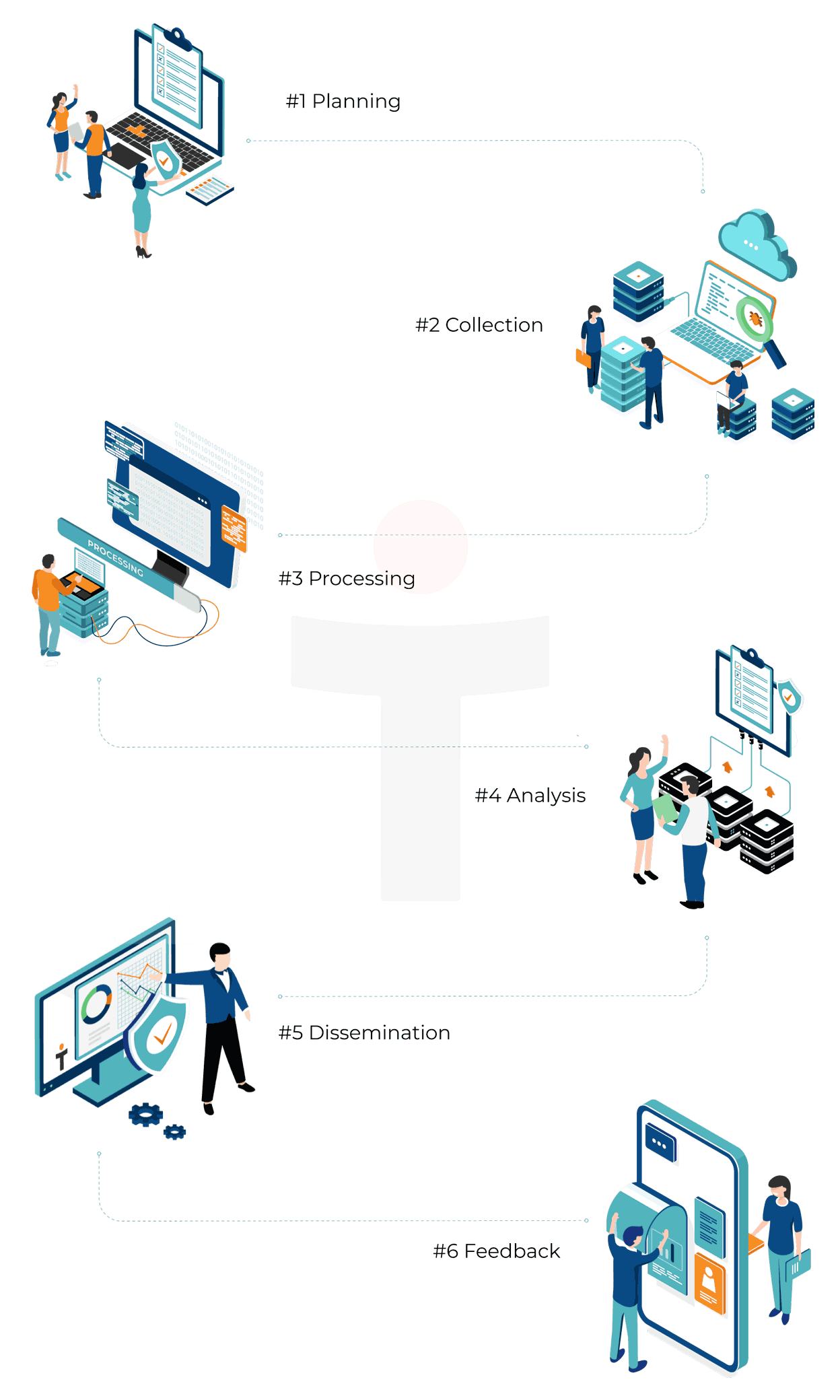
With StickmanCyber, the threat intelligence lifecycle has six key stages:
#1 Planning: We set out the goals, objectives and methodology for collecting threat intelligence based on the requirements of key stakeholders. It involves identifying who the attackers are, their respective motivations, possible attack surface, and what measures need to be taken to improve defenses against a potential attack.
#2 Collection: We set up systems and processes to collect the data required, from a wide range of sources both internal and external, to satisfy the objectives defined in the first stage. It is important that teams collect data
#3 Processing: Essentially evaluating the data’s reliability and relevance before it can be analysed. This stage involves sorting and organising the data, which may include removing any false positives or redundancies.
#4 Analysis: We analyse the available data to arrive at answers to the questions created in the planning stage of the life cycle. The main objective of this stage is to convert processed data into the context required for the intended audience i.e. valuable recommendations and action items.
#5 Dissemination: The StickmanCyber threat intelligence team presents their analysis in a report format fit for the intended audience outlined in the planning stage. For example, if the audience is executive management, then the threat intelligence needs to be in a format that can be easily consumed i.e. no technical jargon and concise, to the point.
#6 Feedback: We take feedback on the provided report to determine whether improvements need to be made for future threat intelligence activities. Stakeholders may have changes to their priorities or adjustments to how data should be disseminated or presented.
Resources
Arm yourself with up-to-date information and insights into building a successful cybersecurity strategy, with blogs and webinars from the StickmanCyber team, and industry experts.
Creating a Cybersecurity Strategy for your Organisation
Throughout the webinar, Ajay Unni, CEO & Founder at StickmanCyber, uses a number of real-world examples to highlight the strategies that work (and why), the most common mistakes organisations make when designing and building a strategy and the pitfalls of implementation without the right internal backing.
Ready to Upgrade Your Cybersecurity Posture?
Know your exact challenge and want a solution partner? Just starting out on the cybersecurity journey? The StickmanCyber team can help.