SOCIAL ENGINEERING: Indicators of Social Engineering
Don’t let your team fall prey to smooth-talking hackers. Train and sensitise your teams, and establish the right protocols to thwart social engineering hacks.
- Home »
- Proactive cybersecurity »
- Social engineering
What is Social Engineering? Social Engineering Examples
Social engineering is essentially manipulating individuals to divulge security information that can be leveraged to access your business systems. Hackers often choose their target, learn about them, and then pose as an expert or a co-worker to trick them into sharing data or credentials.
Such hacks are becoming increasingly common because it’s easier to con humans than to bypass network security.
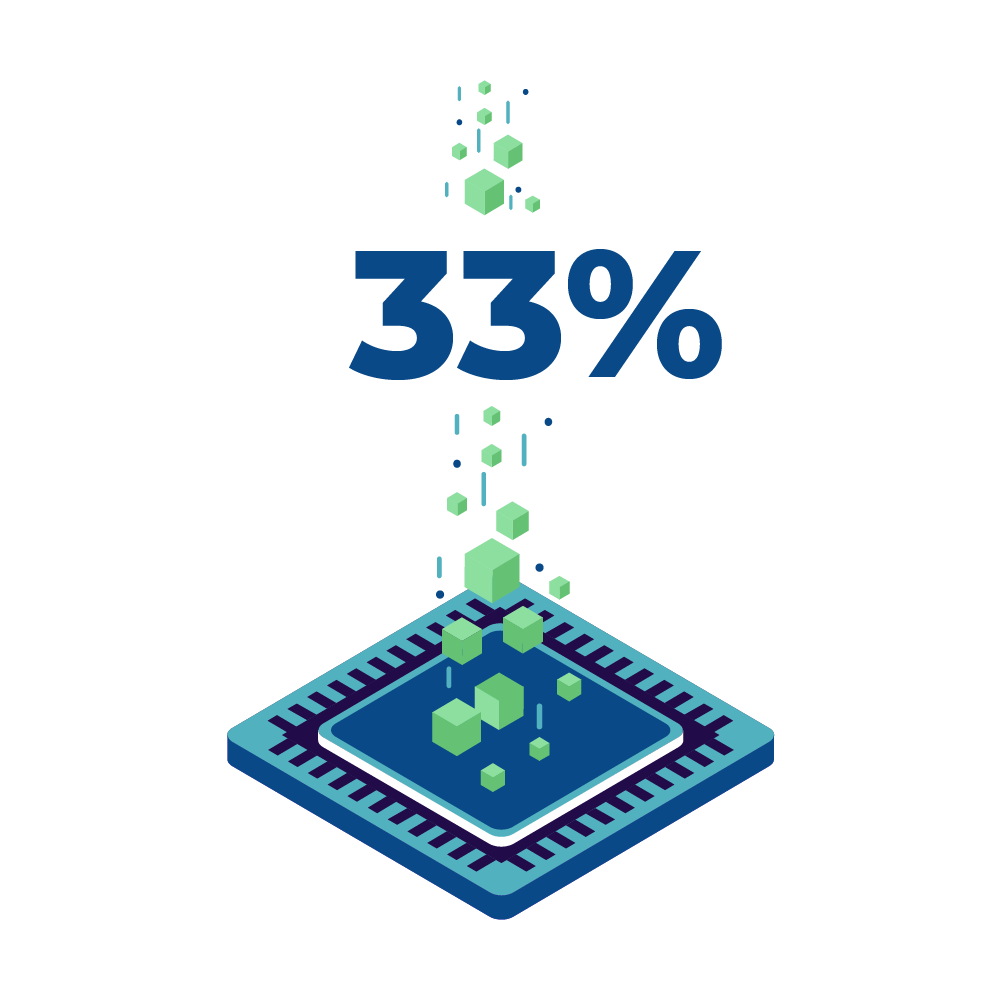
That’s the share of social engineering hacks in total cybersecurity breaches.
Are you vulnerable? It’s time to find out, and take action!
StickmanCyber can help sensitise your teams to the range of probable social engineering hacks, and how to spot them. Most employees usually are not even aware of the possibility that hackers can trick them into disclosing privileged information. And hence, it is important for organisations to focus on training their employees to identify and avoid falling prey to this tactic.
The Range of Social Engineering attack

Types of Phishing
An attacker sends an employee a fraudulent message via email, instant message or text message. An unaware employee can end up clicking a link that downloads malware onto their system, freezes the system as part of a ransomware attack, or reveals sensitive information about the organisation.

Watering Hole
The attacker identifies a website that is commonly visited, and therefore trusted by employees. They then proceed to infect the website with malware and wait for one of the employee systems to become infected. Once infected, the attacker can now access the employee’s system.

Whaling
This is a social engineering tactic used by cyber criminals to ensnare senior or other important individuals in an organisation by acting like another senior player, in the hopes of gaining access to their computer systems or stealing money or sensitive data.

Pretexting
An attacker creates a scenario or pretext to engage with the targeted employee and psychologically manipulates them to share valuable information. Or to perform actions that would be considered out of the ordinary in a normal situation.

Quid Pro Quo
Attackers pretend to offer victims a service or benefit if the latter performs specific tasks or gives out information or access. Attackers usually masquerade as IT support and convince employees to type in commands onto their device that gives the attacker access to company systems.
Take Action Now!
Prepare your teams to spot and avoid social engineering hacks. Invest in your cybersecurity and bring in the experts today!
How We Do It
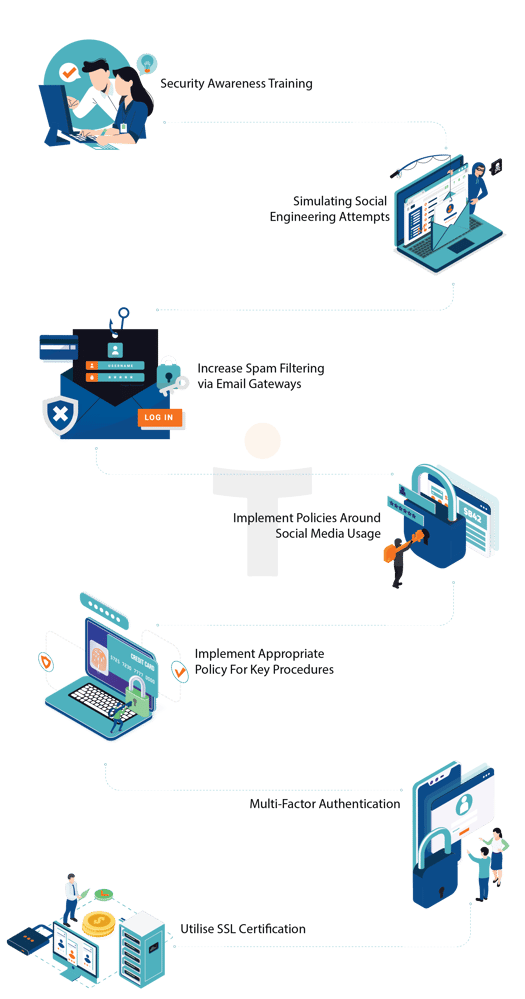
StickmanCyber helps your organisation implement a set of key best practices to help thwart social engineering hacks:
- Security Awareness Training: We host workshops where we train your employees in spotting common red flags that can help them identify popular social engineering tactics amongst cybercriminals.
- Simulating Social Engineering Attempts: Go a step ahead and do multiple simulations of possible social engineering scenarios, to improve your teams’ ability to spot the tricks.
- Increase Spam Filtering via Email Gateways: Most social engineering hacks come in via emails. We help implement the right email gateway to identify and categorise such emails as scams.
- Implement Policies Around Social Media Usage: Given that most hackers approach their targets on social media, we can help create well-defined policies on what employees can and cannot share over such platforms.
- Implement Appropriate Policy For Key Procedures: We can help craft and implement appropriate policies when dealing with procedures like transferring money or making payments, to reduce the success rate of social engineering hacks.
- Multi-Factor Authentication: Our teams can implement multi-factor authentication to reduce the chances of hackers gaining access with just the information gained via social engineering.
- Utilise SSL Certification: Our experts can help obtain the right SSL certificates to encrypt data and minimise the impact of cyberattacks.
Resources
Arm yourself with up-to-date information and insights into building a successful cybersecurity strategy, with blogs and webinars from the StickmanCyber team, and industry experts.
Top 10 Cybersecurity Uplift Focus Areas 2021
In this webinar, Ajay shares key insights, learnings and takeaways from the 100’s of projects run and executed by StickmanCyber’s and industry knowledge from the last 12 months culminating in the Top 10 investment focus areas organization’s need to have in place for 2021-2022 when it comes to improving and uplifting their cybersecurity posture.
Ready to Upgrade Your Cybersecurity Posture?
Know your exact challenge and want a solution partner? Just starting out on the cybersecurity journey? The StickmanCyber team can help.